In today’s “work from anywhere” model, cloud-based identity management solutions are quickly becoming the norm. To enable interoperable Cloud provisioning, Microsoft has embraced System for Cross Domain Identity Management (SCIM) protocol in Azure. SCIM was created as a powerful means of standardizing, simplifying, and automating identity management of users, groups, and devices across cloud-based applications and services, and Microsoft is betting big on it. The problem with SCIM is that it has yet to become widely adopted, and many applications simply do not support it. Suppose you have custom applications with repositories of identity information or use an on-premise or cloud application like SAP S/4 HANA or SAP Ariba or even a major HR system like UltiPro. In that case, you will not be able to integrate those systems with Azure unless you or the vendor builds a SCIM interface for each. This is no small task, because while the protocol is simple, building the interface is not. EmpowerID has stepped into the gap and built a Workflow-Driven SCIM Virtual Directory Server (VDS) that can sit between Azure and your non-SCIM applications. You simply connect those applications to EmpowerID and register the EmpowerID SCIM VDS in Azure. There is no need to wait for vendors or put in the time and effort needed to build a SCIM interface. EmpowerID takes care of everything for you.
WATCH A SHORT OVERVIEW OF OUR
WEBINAR ON AZURE IDENTITY MANAGEMENT
Azure Identity Management
Azure Active Directory has grown in importance from merely being one of an organization’s directories to becoming the hub for all of an organization’s applications and digital identities. As organizations undergo a “Digital Transformation” in how they operate, the work of IT has grown more complicated by new challenges to deliver access and ensure compliance for an ever more complex web of on-premise and Cloud applications at all times. Azure Active Directory is now at the heart of these efforts and a new breed of Identity Platform is required to ensure its success.
Easy Integration for All Your Identity Aware Applications
By adopting SCIM as the identity protocol, Microsoft paved the way for integrating any SCIM compliant application with Azure.

Their aim is to make Azure AD the central point for authentication, conditional access, and MFA. They want you to use Azure AD for all your identity-aware applications. While this sounds great, the reality is that many vendors have yet to adopt SCIM. And without SCIM adoption, there is no way to connect their applications to Azure AD. That goes the same for any non-SCIM applications your organization may have developed. You must either wait for vendors or invest the time and effort into developing a SCIM framework yourself. For most organizations, this is simply not feasible.
This is where EmpowerID comes into the picture. We are the first company to create a stable, fully functioning SCIM Virtual Directory that allows you to connect all your identity-aware applications to EmpowerID, and then by virtue of your connection to EmpowerID connect to Azure AD.
How does this work?
The SCIM Virtual Directory is a microservice and a SCIM server created by EmpowerID that can be deployed as an App Service in Azure tenants. This makes the SCIM VDS the go-between for Azure and any applications registered in EmpowerID. Provisioning calls are made to the EmpowerID SCIM VDS, and the call is then directed to the appropriate system.

For example, if you have connected EmpowerID to Salesforce and an HR system and a new user is provisioned in Azure AD, EmpowerID intercepts the call to provision the new user and directs it to the appropriate systems in EmpowerID.
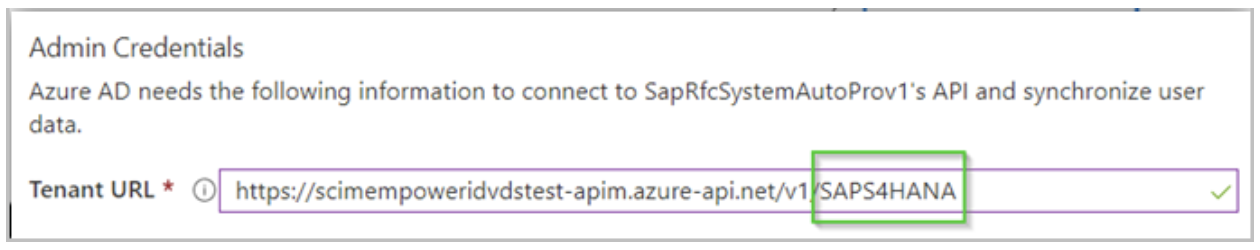
This allows for any policies and other business logic to be evaluated first. Once your business logic completes, the account is provisioned in the appropriate systems, and everything is kept up to sync. The natural question arises as to how EmpowerID knows what system to update. The answer to the question is the URL you set for your applications in EmpowerID. Without going into detail, you simply specify the path to the application registered in EmpowerID. The below image depicts this.
The last part of the path points to the application in the image. This is how EmpowerID knows where the direct the call made by Azure.
This allows you to SCIM-enable any system connected to EmpowerID without needing to create a specific SCIM connector for that system. EmpowerID does it for you, helping you leverage Azure AD provisioning quickly and easily for many systems with some advanced features.
WORKFLOW-DRIVEN VIRTUAL DIRECTORY SERVICES
Traditional SCIM connectors simply “fire and forget.”

They pass commands from one system to another and leave it at that. There is no middle layer of logic involved. In other words, they are more of a SCIM gateway. The EmpowerID SCIM VDS takes another approach. Not only does it pass commands from one system to another, but it evaluates your business processes while doing so.
We call this approach “everything is a workflow,” and it is central to the EmpowerID paradigm. Organizations need to inject their business logic into the process to have complete control.
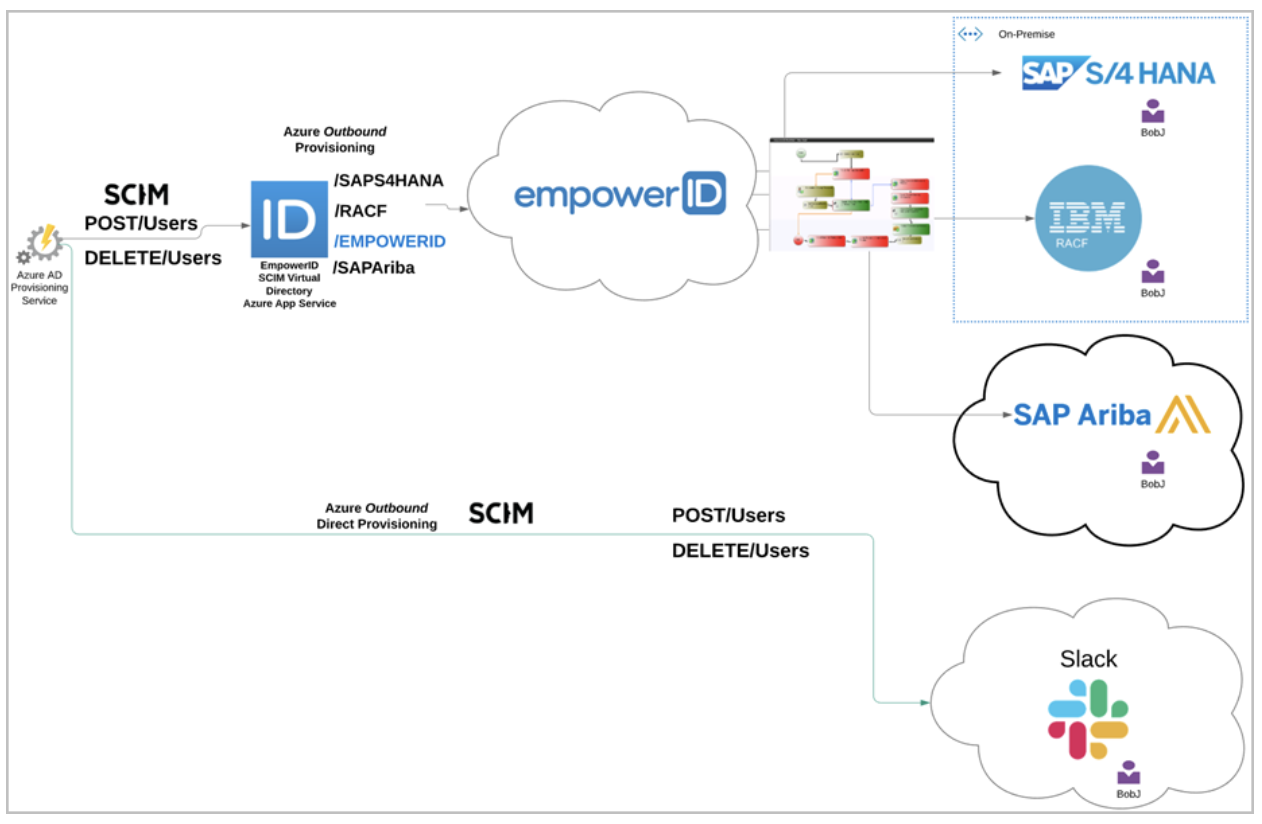
The above image depicts the difference between the two approaches. Azure AD Provisioning Service sends commands to the EmpowerID SCIM VDS in the first flow. EmpowerID then invokes the workflow appropriate to the command where business processes can be executed before sending those commands downstream to a connected system. In the second or lower flow, Azure sends the same commands to a directly connected system and they simply happen in that system. There is no control over the transactions. With EmpowerID standing in the middle, the entire process is can be evaluated and interrupted if need be.