EmpowerID Privileged Session Management & Zero Standing Privileges:
Request a Demoto see our Advanced PAM offering!
Controlling Access to Servers and Tools
EmpowerID extends Basic PAM functionality, allowing admins to temporarily log in to servers using vaulted credentials in a Privileged Session Management recorded session. Typically, PSM grants full desktop console access enabling the admin to run any tools or scripts. EmpowerID PSM adds an additional level of control, allowing the admin to launch only single applications in PSM sessions when less access is required.
Another EmpowerID tool to extend Basic PAM functionality is the Privileged Application Launcher (PAL). PAL enables admins to launch specific applications on their workstations using vaulted credentials. The admin can select a vaulted credential and the local application they wish to run using that privileged identity. Admins can run computer and directory administration tools and launch PowerShell sessions and cmd sessions using vaulted credentials that are not revealed.

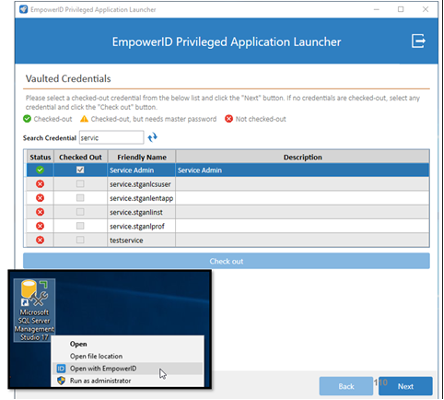
Figure: Privileged Application Launcher starting the SQL Management tool as a DBA admin.
Both approaches can help prevent admins from performing unauthorized activities during a temporary session but are still classified as Basic PAM because they rely on pre-provisioned privileged accounts. EmpowerID includes the option to provision a just-in-time privileged account that is deleted at the end of the session, eliminating the risk of standing privilege.
Eliminating the Need for Native Admin Console Access
A significant challenge for most organizations is the high number of standing privileged accounts required by helpdesk and administrative staff to perform routine identity-related tasks across their hundreds of applications and Cloud application platforms.
"Cloud Management consoles, like those on Azure, AWS, and GCP, pose significant security risks to every company if not managed well. Over-privileges are a common fact, and most organizations lack granular visibility into whether privileged users have unnecessary entitlements and provisions."
Martin Kuppinger, Founder and Principal Analyst at KuppingerCole
The standard approach is to grant standing native direct privileged access to each of these platforms and then train IT staff how to use each. This violates the principles of Zero Trust, creating a huge security risk and consumes an undue portion of the IT budget as this user population is often outsourced and experiences high turnover. High turnover creates many opportunities for privileged orphan accounts to remain active and accessible for long periods. A steady stream of new staff requiring training on the hundreds of native application and platform console interfaces for performing their duties generates a significant expense.

Four major challenges are encountered by enterprises granting native admin console access:
- Security vulnerabilities that arise from requiring overly privileged standing accounts to perform routine identity and computer administration tasks.
- Costly training due to the lack of a single easy-to-use management interface and security model for managing Cloud and On-Premise applications.
- The inability to view a user's current access across all platforms in an understandable way. And the capability to transform this access into a just-in-time model granting only the granular access needed to perform authorized activities.
- Automating detailed processes that are both subject-to-error and time-consuming.
EmpowerID leverages its long history and mature functionality for Privilege Elevation and Delegation Management (PEDM) and Privileged IT Task Automation to break the risky cycle of granting standing access and continuously retraining a new IT staff. EmpowerID was founded as a low code Privileged IT Task Automation platform to eliminate the need to grant direct unproxied native access to servers and admin consoles for performing routine identity administration tasks.
EmpowerID achieves this by providing internal or outsourced IT admins a single workflow-driven web-based user interface with which they can perform the most common identity-related tasks across their critical on-premise and Cloud platforms. A single user interface and granular task-focused security model with object-level privacy and centralized activity logging eliminate the risk and expense of granting native admin permissions and training staff on the 100's of applications and idiosyncratic security models for which they are responsible.
As an example of the granularity possible with this functionality, a project developer could request access in the EmpowerID IT Shop microservice that would allow her to manage just the assignment of a single Azure RBAC role scoped to a single Resource Group in one tenant for a handful of IT project users. This access would be temporary, and all activities would be performed only in the EmpowerID web interface with no native access to the Azure portal or any roles being granted.
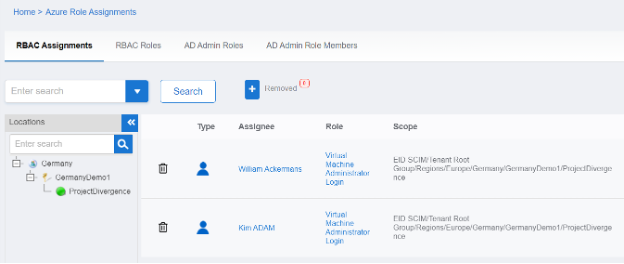
Figure: Constrained access to perform Azure privileged activities
As another example, common tasks such as requesting Managed Identities would require high level administrative privileges but they can be automated and even published as self-service request processes with flexible workflow approvals and tracking.
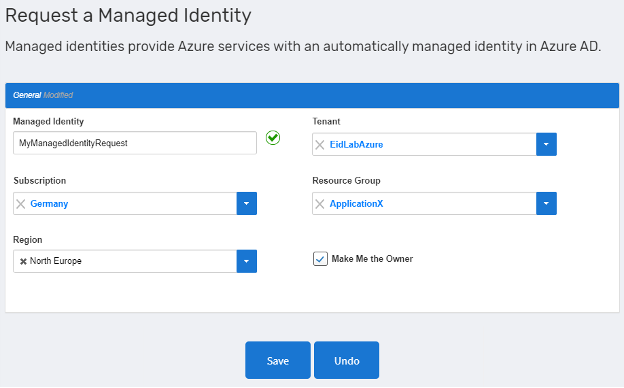
Figure: EmpowerID's example of self-service request for an Azure Managed Identity
These are just two examples of how EmpowerID can delegate and automate fine-grained IT tasks without granting native access or requiring the user to learn a multitude of tools. EmpowerID offers over 1,000s workflows to enable these types of activities across all major platforms and applications (e.g., Azure, GCP, AWS, ServiceNow, SalesForce, SAP, Active Directory, etc.). It is easy to see how having a single solution eliminates complexity, reduces training costs, avoids human error, and reduces risk across all your major platforms is a valuable component in any PAM strategy.
Cloud Infrastructure Entitlements Management (CIEM)
EmpowerID's Advanced PAM has expanded into a new category of functionality known as Cloud Infrastructure Entitlements Management (CIEM). Cloud platform identity entitlements are often much more complex and granular than in traditional applications and server access. This complexity is magnified when we must consider that most organizations are multi-Cloud and even multi-vendor Cloud. Traditional PAM solutions are not designed to inventory and understand the complexities of who has access to what across these Cloud landscapes or to implement least privilege controls, assess and monitor risk, and provide governance.
EmpowerID has a purpose-designed data model, known as Universal Policy-Based Access Control (UPBAC), which was created to support ingesting the most complex and fine-grained Cloud entitlements and resources from systems such as Microsoft Azure, SAP S4/HANA, AWS, SalesForce.com, and others. By unifying the fine-grained permissions model of such diverse systems into a single Identity and Entitlement Warehouse, organizations can visualize, understand, and manage the impact and risk of access across these diverse multi-Cloud landscapes.
Using the entitlements model of Microsoft Azure as an example of the need for a more sophisticated CIEM approach, we can see that there are many more identity types and role types within the Azure platform which must be scanned and managed to truly assess risk and control access. Solutions which stop at the traditional user and group level, will have an incomplete picture of privileged access and be unable to grant access on a fine-grained least privileged basis.
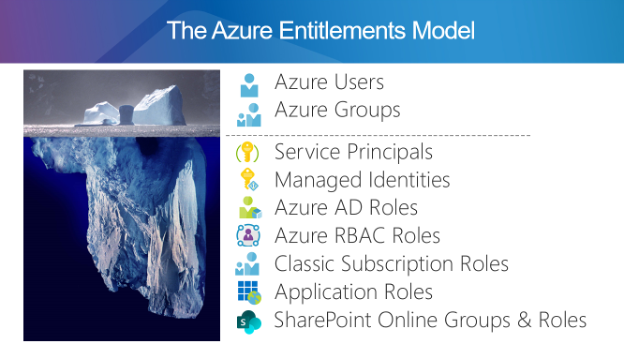
Figure: EmpowerID's example of the Complexity of Cloud Entitlements
EmpowerID's CIEM functionality goes deep into the unique permissions model and policies for each major platform. For Azure this means to go deep into the new types of identities, the hierarchical management group and subscription structure of each tenant, the roles and their fine-grained permissions, and even the resources such as applications and workload. The UPBAC model, consumes this entitlement structure and uncovers the human understandable access, the associated risks, and enables organizations to implement a Zero Standing Privilege model which grants fine-grained targeted access just in time.
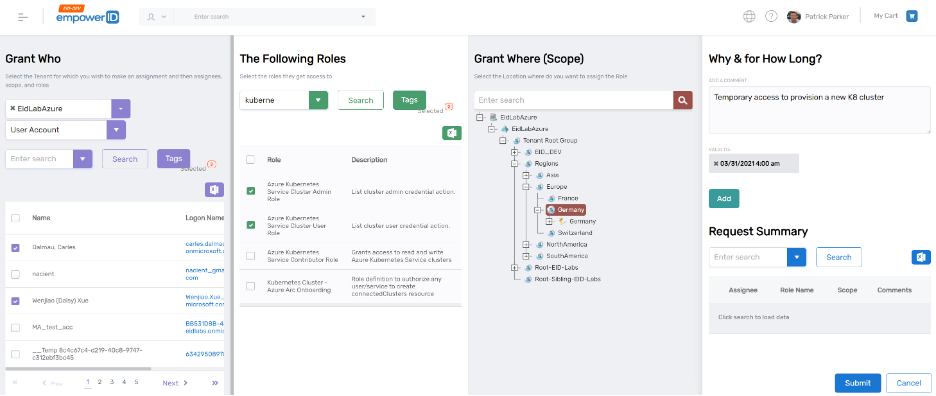
Figure: EmpowerID's example of workflow to grant fine-grained Azure access
The Identity Analytics engine in EmpowerID, maps fine-grained permissions across various Cloud platforms to a single unified and risk-assess set of functions or activities. This translation provides a common language for IT admins requesting access, business managers approving access, and IT auditors that assess and manage risk.
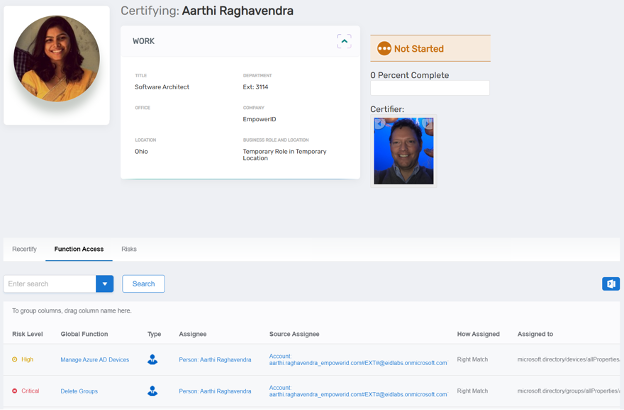
Figure: EmpowerID's Functional Access View Assisting Recertification
Given the complexity these Cloud platforms represent, a purpose built tool such as EmpowerID has become a necessity to ensure compliance and manage entitlements across these diverse systems.

