On December 15th, 1999, Microsoft released Active Directory. It quickly became the central hub for most organizations to manage the security for their users, applications, and computers. Given that 85% of all organizations use AD, it is the foundation of cyber security and privileged access (Paramount Defenses Inc., 2016). However, with such exalted status comes increased risk and, as a result, organizations require the ability to investigate, evaluate, and manage their systems.
In this article, we will look at how EmpowerID helps organizations to accurately, frequently, and efficiently assess, audit, and manage their Active Directory and Azure Active Directory security.
Active Directory Security Assessments
An Active Directory Security Assessment (ADSA) is a simple methodical assessment that your organization can conduct to assess the security of your foundational Active Directory. It assists your organization in identifying, quantifying, and reducing the risks affecting your AD.
Purpose of an ADSA
When you first construct your Active Directory forest, it is pristine and current. Unfortunately, that is as good as it’s going to ever get.
Moreover, for a quite sizable proportion of organizations, their AD likely dates to the earliest age and is also far from being either pristine or current.
Either way, as soon as your AD is used in earnest, whether by adding users, operating systems, applications, locations, and other content, it loses that newness and efficiency.
For the unwary, especially, it can rapidly become worn out and weathered and with reduced performance. Peter Drucker, the science of business management guru, is famously quoted as saying that “you can't manage what you can't measure.”
What Drucker meant is that you can't know whether you are successful unless success is defined and tracked. A cluttered directory is inherently a security risk due to the security implications of clutter – orphan accounts, excess privilege accumulation, and unnecessary groups.
Azure Clouds the Issue
Unfortunately, migrating to the cloud and implementing an identity management solution compounds these problems. Not least because of security issues, dependencies, compatibility, etc., but also because of the data synchronization itself.
Unless you comprehensively analyze your system prior to migration and the implementation of an identity management tool, then you are replicating what you have locally—errors, mistakes, bloat, and every other item of chaos your AD contains. When you then add in your B2B, B2C, customers, partners, Office365 groups, etc., it is far from being an ideal position to be in.
Nobody builds an IT infrastructure that intentionally exposes the organization to compromise or to be inherently ineffective. But, and this occurs more frequently with larger organizations, AD can expand to the extent and at such a rate that the risk of both increases—often quite dramatically.
Almost to the extent that costs escalate and can even spiral out of control. Where the latter is concerned, projects are prone to such risk.
The Project Deprovisioning Security Risk
Projects are particularly problematic. Once the project delivers, it winds down and all team members then disperse to other tasks. All too frequently, however, their rights and entitlements are not disabled or removed—they retain full provisioning. Not only does this create both additional cost and risk for the business but also, in many cases, when you consider the number of projects involved, it is yet further compounded.
ADSA Can Assist Your Organization in Several Ways
Naturally, it cannot ever be in the organization’s best interests to continue such practices. Yet, without an efficient means of performing Active Directory Security Assessments that is the reality with which they are faced.

At best, this will be expensive, there will be a huge administration overhead, and it will become increasingly difficult to manage. At worst, it poses what constitutes a completely unacceptable security risk and could even mean that your organization is no longer compliant.
That is why an effective ADSA is critical to the success of your organization. To be effective, ADSA needs to meet 3 specific objectives.
Objectives of an ADSA
The 3 specific objectives for security assessments are to:
- Obtain an expert’s perspective on exactly what issues you should address first.
- Optimize your environment to detect issues before they arise (based on Microsoft’s best practices).
- Establish a baseline so you can track your progress throughout the year.
Having established what the objectives of an ADSA are, what benefits does an ADSA offer?
The Benefits of an ADSA
When your ADSA meets the defined objectives, above, it is possible to garner significant benefits:
- Achieve major cost savings through leveraging prioritized, actionable guidance to help secure existing investments. (This contrasts with the increasing cost and complexity of adding additional and unnecessary security components to an already secure AD implementation.)
- Provide a snapshot of the Active Directory security configuration at a point in time—this snapshot permits you to see exactly what is in place within your organization, what still needs to be done, as well as helping you to meet audit requirements.
- Identifies the most common and effective attack vectors and explains how best to detect, mitigate, and prevent them—after all, forewarned is forearmed.
- Offers tailored recommendations for leveraging existing technology investments to improve your organization’s overall security posture—expert guidance and advice on how you can modify your exisiting setup ensures that you are not only getting the best out of your existing systems, but it also highlights specific areas of attention.
- Identifies top security issues and provides guidance on the best methods to mitigate and resolve them—as above, being aware of and knowing current threats provides advanced notice and enables remedial or other action to be implemented.
- Provides a detailed report of the issues discovered and their impact along with recommended remediation—expert advice and recommendations for what needs to happen helps you to best prepare your organization’s defence.

Effective security assessments are a vital arm in your organization’s defenses and can make the difference between either plugging and blocking previously unknown or overlooked gaps or the attacker exploiting and, potentially, laying bare your critical systems.
What Advantages Does EmpowerID’s ADSA Provide?
You gain several advantages quite simply because of the way we designed and built EmpowerID. EmpowerID is a purpose-built system that:
- Leverages a powerful Identity Warehouse and Active Directory connector to perform a comprehensive analysis of Active Directory.
- Utilizes automated information-gathering jobs and analysis tools to gather indepth information about the configuration of the directory, privileged accounts, security settings, domain controller configurations and even the inappropriate use of privileged accounts.
- Performs expert analysis on collected data reports and provide recommendation and remedial actions for security risks.
What does EmpowerID assess?
Out of the box, EmpowerID assesses the following:
- Expired user accounts
- Disabled user accounts
- Inactive user accounts
- Duplicate user accounts
- Service Identity User Accounts
- Local Computer Admin User Accounts
- High Security User Accounts
- User Accounts that never logged in
- Empty groups
- High security groups
- Groups containing only disabled or expired user accounts
- Expired groups
- Members of high-risk groups (resultant members of Domain Admins, Enterprise Admins, Administrators)
- Generate reports of which groups the executive board’s domain user account belongs.

These enable you to fully analyze and assess your AD and Azure AD systems.
However, and as we will look at next, you can also add and assess additional attributes.
What other attributes can we add?
-
Group membership comparisons — this is an intersection to determine which users are in multiple groups. For example, you could compare the temporary contractors group with the all employee’s security group to determine if, somehow, there was accidental crossover.
This comparison uses the same logic as that of Separation of Duties (SoD) where your business policies determine what is acceptable to the business, and what is unacceptable (the latter being a toxic combination). -
Inventory Rights/Permissions — to find granular assignments of high-risk access such as:
- Replicate Directory Changes
- Replicate All Directory Changes
- Reset Password
- Unconstrained Delegations.
The ADSA process comprises 3 steps and is as follows.
The EmpowerID 3 Phase ADSA Process
The assessment process has 3 primary phases:
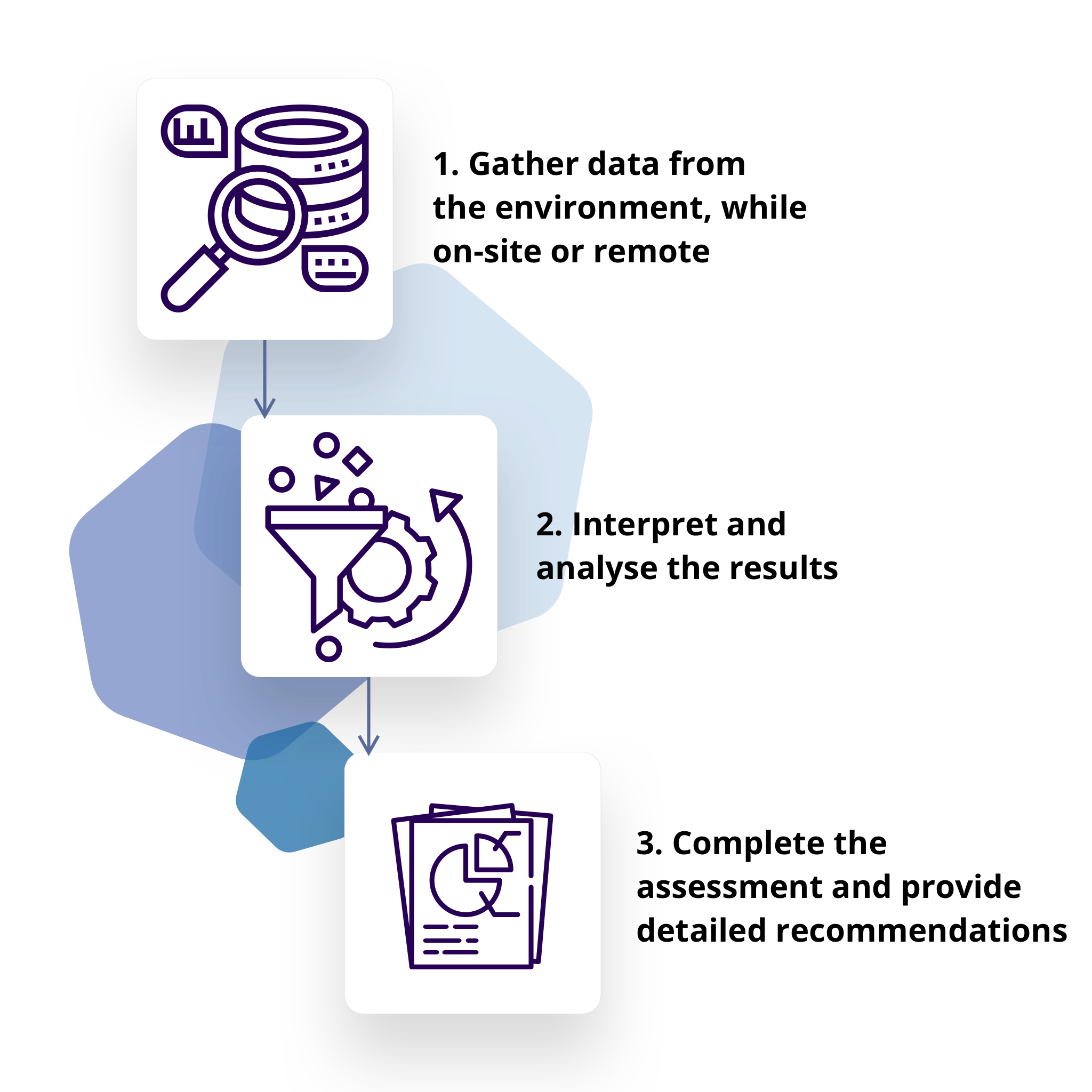
As you can see, EmpowerID’s ADSA covers many areas, helping to ensure that nothing is inadvertently overlooked. Identifying the clutter and security vulnerabilities is but the first step. EmpowerID also offers a powerful cleanup capability as a SaaS solution.
Conclusion
Maintaining your AD, whether on-premise or in the cloud, is both crucial to your organization and requires you to employ the right tools. Tools that not only always assess the security status of your system but can also make recommendations for improvement based on that status. However, with your Active Directory, it is critical that it is optimized. If not, its performance will suffer, delays will occur, and your costs will escalate.
Here at EmpowerID, we are fully aware of the requirements, complexity, and difficulty of both maintaining and optimizing your AD. That is exactly why we designed and invented the tools to make this simple, easy, and efficient. We are sure you can see the enormous capability that EmpowerID offers. We also hope that you can see that it is no exaggeration when we say what EmpowerID offers is both unique and a gamechanger.
Next steps
If you would like to learn more, then feel free to contact us. We will be delighted to hear from you and look forward to answering all your questions.
Links mentioned in this post
If you want to delve more into the other components of EmpowerID, links to related topics and information are below:

