-
 EmpowerID helps SIEMENSDOWNLOAD CASE STUDY
EmpowerID helps SIEMENSDOWNLOAD CASE STUDY
achieve Zero Trust
AND Secure the World’s
Largest Azure Active Directory -
 Approaches for externalizing authorization using RBAC, ABAC, and
Approaches for externalizing authorization using RBAC, ABAC, and
PBAC are discussed and illustrated, highlighting their strengths,
weaknesses, and where each performs best. In summary, a methodology dubbed
Compliant Access Delivery is proposed, combining the best of RBAC, ABAC, and PBAC
with the principles of Zero Trust and Least Privilege. (60 pages read)
A Guide to AuthorizationDOWNLOAD WHITEPAPER -
 If your organization is contemplating an IAM solution then there
If your organization is contemplating an IAM solution then there
are certain pitfalls that you need to be conscious of. Being aware
of, and avoiding, these will aid you in making a good choice,
not least in understanding, planning, and in timesaving.
IAM Best PracticesDOWNLOAD WHITEPAPER -
 Find out how our new Azure License Manager can help you save
Find out how our new Azure License Manager can help you save
up to 50% on Microsoft Office 365 license costs by identifying
and reallocating all inactive, over sized and duplicate licenses and
automating license management using flexible policies.Azure License ManagementDOWNLOAD WHITEPAPER -
 Find out how our Azure RBAC Manager empowers organizations
Find out how our Azure RBAC Manager empowers organizations
to maintain an accurate understanding of their Azure security
landscape to ensure compliance with an organization’s risk policies.Azure RBAC ManagementDOWNLOAD WHITEPAPER -
 We know that comparing products in general, let alone in IAM,
We know that comparing products in general, let alone in IAM,
can be awkward. A such, we’ve tried to make this easy to read and reference.Competitive ComparisonREAD MORE -
 This Leadership compass focuses on the market segment of Identity-as-a-Service (IDaaS) with a focus on
This Leadership compass focuses on the market segment of Identity-as-a-Service (IDaaS) with a focus on
IGA (Identity Governance and Administration, i.e. Identity Provisioning and Access Governance) technologies.Identity as a Service, IGA in theREAD MORE
KuppingerCole Leadership Compass -
 Outdated security modes and methods are proven to be ineffectual and,
Outdated security modes and methods are proven to be ineffectual and,
quite simply, no longer work...Identity Is the New Perimeter,READ MORE
Zero Trust is its Firewall -
 In 2017, 88% of breaches were accomplished using nine attack vectors that were identified in 2014.Anatomy of a Cyberattack,READ MORE
In 2017, 88% of breaches were accomplished using nine attack vectors that were identified in 2014.Anatomy of a Cyberattack,READ MORE
“Security mantras” and their effectiveness. -
 EmpowerID Delivers Compliant Access to Cloud
EmpowerID Delivers Compliant Access to Cloud
and On-Premise Applications.The only Zero Trust Full Identity Platform,GET STARTED NOW
Identity Evolved -
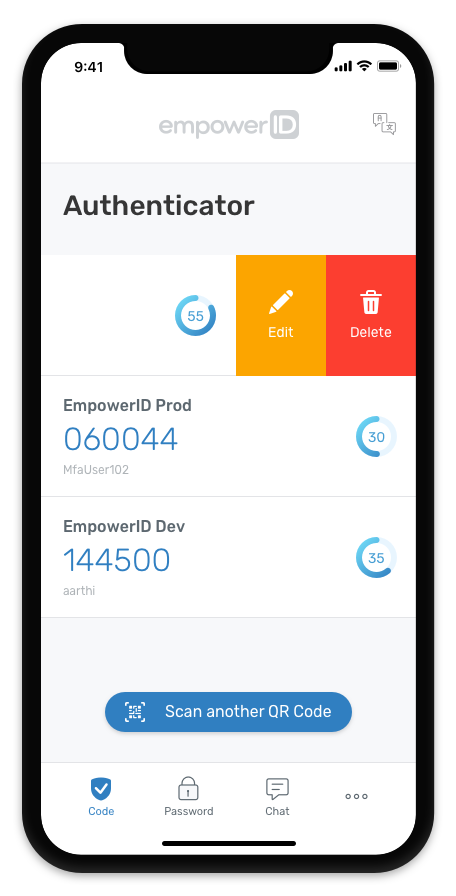
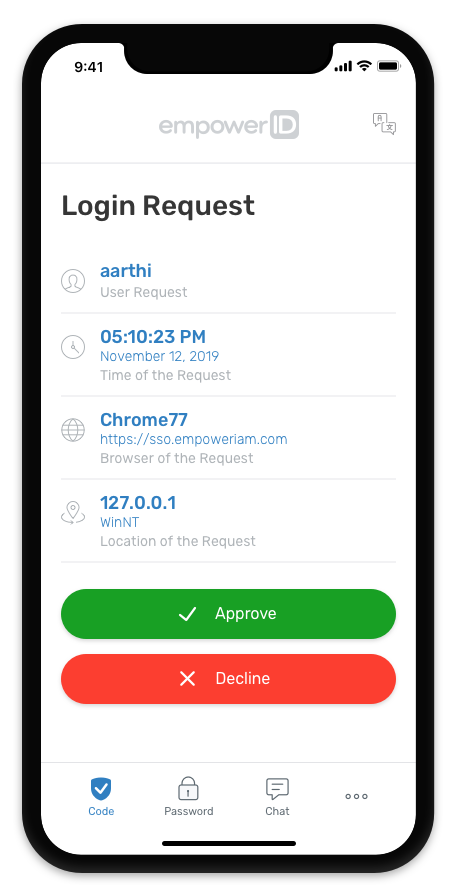
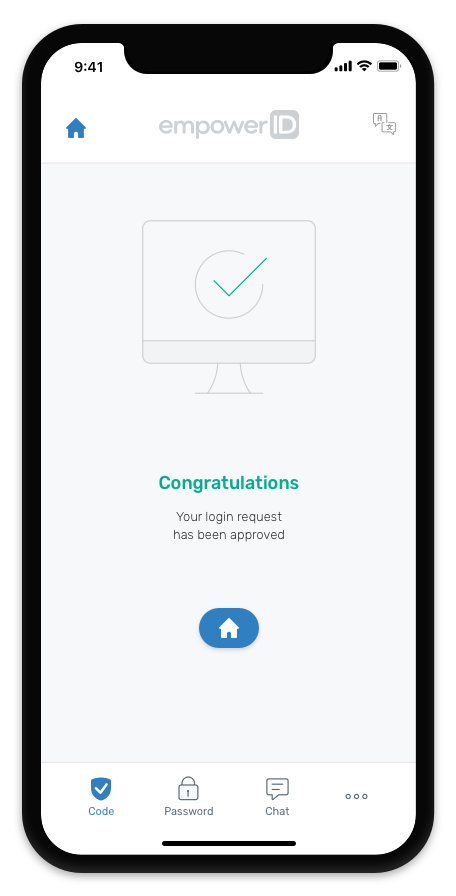
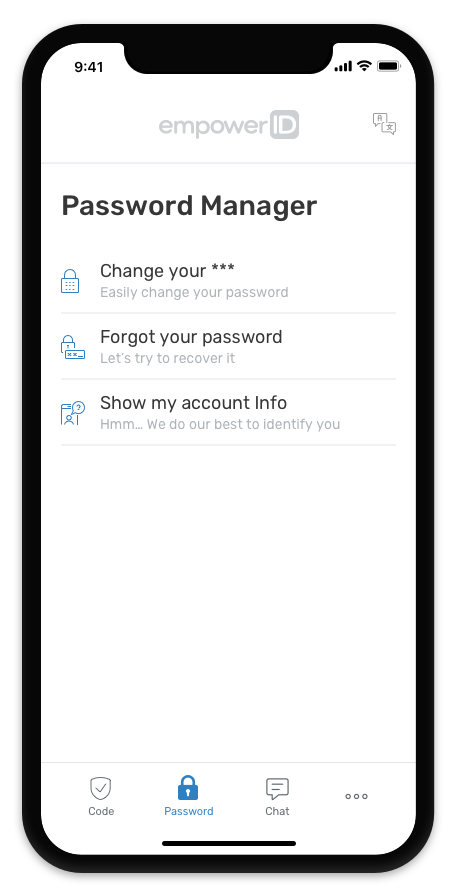
 the EmpowerID Mobile App provides multi-factor
the EmpowerID Mobile App provides multi-factor
authentication (MFA) and chatbot help.Identity Management and Cloud Security,DOWNLOAD
EmpowerID Mobile APP
The only Zero Trust Full Identity Platform EmpowerID Delivers Compliant Access to Cloud and On-Premise Applications.
EmpowerID serves Healthcare Banking & Finance GOV & Non-profit Manufacturing industries
Integrations
EmpowerID
EmpowerID is the award winning, all-in-one Identity Management and Cloud Security suite.
With over two decades in the industry, we are trusted and deployed in many of the world's largest organizations.
Most security initiatives are compliance-driven focusing on paperwork, not actual security.
We provide a highly scalable, fully customizable IAM infrastructure that delivers results in a more time and cost-efficient manner for your enterprise. Accolades include: “Product leader, Innovation Leader, and Overall Leader”
EmpowerID allows organizations to stop worrying about account management, audit, and policy enforcement, and get back to doing business.
Company
Customer Success Stories

Retail Customer Story
With over 5,300 stores in 80 regions around the globe, this client is a major player in the retail market.

Aerospace Customer Story
A global multinational aerospace corporation, this client is both a household name and a worldwide leader in their field.

Healthcare Story
Serving medical healthcare providers in the Pacific Northwest, this client of ours is a recognized name and a large healthcare community portal.
EmpowerID Privileged Session Management & Zero Standing Privileges
Overview of PSM and how organizations can move towards a Zero Standing Privilege model
EmpowerID Multi-Factor Authentication
Overview of EmpowerID's end-user multi-factor authentication experience
User Managed Access 2.0 and Open Policy Agent
How to authorize using User Managed Access 2.0 with Open Policy Agent as the Policy Decision Point (PDP)
The Jelly Bean Problem
The Challenge of Authorization Management in a Multi-Cloud World
EmpowerID Innovation
Overview of EmpowerID IAM innovations
EmpowerID Identity Lifecycle Management
EmpowerID Intro into Identity Lifecycle Management
EmpowerID Certifications